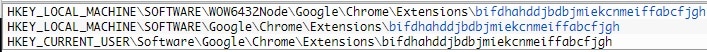
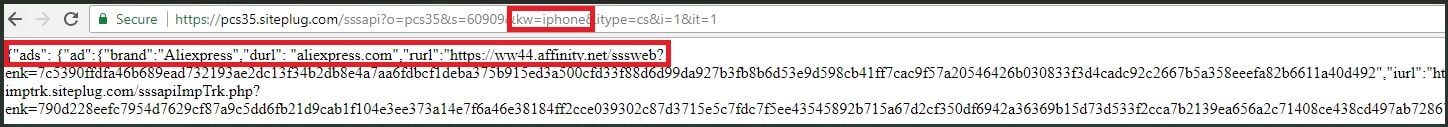
According to their findings, more than 1,300,000 users attempted to download malicious or unwanted extensions at least once in the first half of 2022, which accounts for more than 70 percent of the number of users affected by the same threat during the corresponding period. “Our telemetry shows that the most common threat spread under the guise of browser extensions is adware — unwanted software designed to promote affiliates rather than improve user experience. Such ads are usually based on the browser history to tap users’ interests, redirect them to affiliate pages that the adware developers earn money from or embed affiliate banners and links in web pages,” Kaspersky wrote in a blog post. Apparently, more than 4.3 million unique users were attacked by adware hiding in browser extensions from January 2020 to June 2022, which is approximately 70 percent of all users affected by malicious and unwanted add-ons. Of these, more than 1 million users encountered adware in the first half of 2022. Further, Kaspersky says that the second most widespread threat was malware (a type of computer program designed to infect a legitimate user’s computer and inflict harm on it in multiple ways). “The aim of some malicious extensions is to steal login credentials and other sensitive information. In addition to stealing cookies and data copied to the clipboard, they can function as keyloggers — monitoring software that is able to track and capture everything users type, making it a huge threat to victims’ sensitive data, such as credentials and credit card details,” it added. During the period January 2020 to June 2022, more than 2.6 million unique users were attacked by malware in the guise of a browser extension, which accounts for 44 percent of all users who encountered malicious or unwanted extensions during this period. Please note that the findings are based on only telemetry from users using Kaspersky software, which means that the numbers could be far higher considering users who are using services of other security vendors. Most Common Threat In 2022 WebSearch The ‘WebSearch’ family of adware extensions, detected as not-a-virus:HEUR:AdWare.Script.WebSearch.gen, was the most common threat in the first half of 2022 that targeted 876,924 users. This threat typically mimicked productivity tools for working with documents, such as DOC to PDF converters, document mergers, etc. According to Kaspersky, WebSearch extensions change the browser’s start page so that the user sees a minimalistic site consisting of a search engine and several links to third-party resources, such as AliExpress or Farfetch. The switch to these resources is carried out through affiliate links from affiliated marketing programs, which is how attackers earn money from their extensions. Also, the extension modifies the browser’s default search engine to search.myway[.]com, which can capture user queries, collect and analyze them, and then actively promote the most relevant partner sites in the search results depending on what the user searched for. DealPly-Related Extensions DealPly-related extensions are adware, which is yet another popular extension with cybercriminals that targeted 97,515 users between January and June 2022. Basically, users get infected with DealPly when trying to download a loader of some hacked software from untrustworthy resources. This adware begins with the execution of KMS activators (programs that activate hacked Windows for free) or cheatengine, used to hack computer games. It can also mimic installers of various software, including proprietary software. To provide persistence for its extensions, DealPly creates the following branches in the Windows registry with the value “update_url”=”hxxp[:]//juwakaha[.]com/update”:
This means even if the user removes the extension, each time the browser is launched it is downloaded again and installed on the browser using this path. Note that the browser updates DealPly-related extensions, even though they are installed from third-party servers, and not from the official Chrome Web Store. DealPly also changes the home page of the browser to place affiliate links on it that match the user’s search queries.
AddScript
AddScript is another threat family, hiding under the guise of browser extensions. 156,698 unique users encountered AddScript in the first half of 2022. Although the extensions of this family do have useful functions such as downloading music and videos from social networks or proxy managers, it can also be used to carry out malicious activity. For instance, AddScript disguises the malicious code. When the extension is running, it contacts a hardcoded URL to get the C&C server address. It then establishes a connection to the C&C server, receives malicious JavaScript from it, and runs it covertly in the background. The malware uses JavaScript fetched after installation that can unobtrusively run videos on the victim’s computer, thus increasing ad revenue from the video being “viewed.” Additionally, the AddScript injects affiliate cookies on the host, receiving commission for transactions that happen in the browser. FB Stealer FB Stealer is one of the most dangerous families in browser extensions. Besides the already traditional search engine substitution, FB Stealer can even steal user credentials from Facebook. Kaspersky security solutions detected 3,077 unique users who came across FB Stealer during the period January to June 2022. FB Stealer is installed by the malware rather than by the user. Once added to the browser, it mimics the harmless and standard-looking Chrome extension Google Translate. The Trojan delivering FB Stealer is called NullMixer, which impersonates a cracked software installer, and thus reaches users. The extension files are stored in the resources section of the NullMixer executable and are copied to the %AppData%\Local\Google\Chrome\User Data\Default\Extensions folder during installation. The installer also modifies the Secure Preferences file, which contains Chrome settings, including information about extensions. Once it is done, the extension becomes active. “Similar to previous families, the extension changes the default search engine. In this case, it sets it to hxxps[:]//www.ctcodeinfo[.]com. In addition, the attackers extract Facebook session cookies — secrets stored in the browser that hold identification data allowing users to stay logged in — and send them to their own servers,” wrote Kaspersky. “Using these cookies, they are able to quickly log in to the victim’s Facebook account and hijack it by changing the login details. Once inside the account, the attackers can ask the victim’s friends for money, trying to get as much as possible before the user regains access to the account.” How To Stay Safe While Using Browser Add-Ons? In order to stay safe while using browser add-ons, only use the browser’s official web store to download extensions. Before downloading, check out user comments and reviews of the extensions, and also run a background check on the developer/publisher. Since extensions add extra functionality to browsers, they require access to various resources and permissions. Hence, it is essential to carefully examine the privacy policy and data collection practices of add-on requests before agreeing to them. Lastly, try to restrict the number of extensions used at any point in time and periodically review your installed add-ons. Uninstall extensions that are no longer in use or you do not recognize.